Privacy and security are the most important issues to the popularity of cloud computing service.
In recent years, there are many research schemes of cloud computing privacy protection based on access
control, attribute-based encryption (ABE), trust and reputation, but they are scattered and lack unified logic.
In this project we systematically review and analyze relevant research achievements.
First, we discuss the architecture, concepts and several shortcomings of cloud computing, and propose a framework of privacy protection; second, we discuss and analyze basic ABE, KP-ABE (key policy attribute-based encryption),
CP-ABE (ciphertext policy attribute-based encryption), access structure, revocation mechanism, multiauthority, fine-grained, trace mechanism, proxy re-encryption(PRE), hierarchical encryption, searchable
encryption(SE), trust, reputation, extension of tradition access control and hierarchical key; third, we propose
the research challenge and future direction of the privacy protection in the cloud computing; finally, we point
out corresponding privacy protection laws to make up for the technical deficiencies.
We proposed relevant research achievements. First, we discuss the architecture, concepts and several shortcomings of cloud computing, and propose a framework of privacy protection; second, we discuss and analyze basic ABE, KP-ABE (key policy attribute-based encryption), CP-ABE (ciphertext policy attribute-based encryption), access structure, revocation mechanism, multiauthority, fine-grained, trace mechanism, proxy re-encryption(PRE), hierarchical encryption, searchable encryption(SE), trust, reputation, extension of tradition access control and hierarchical key; third, we propose the research challenge and future direction of the privacy protection in the cloud computing; finally, we point out corresponding privacy protection laws to make up for the technical deficiencies.


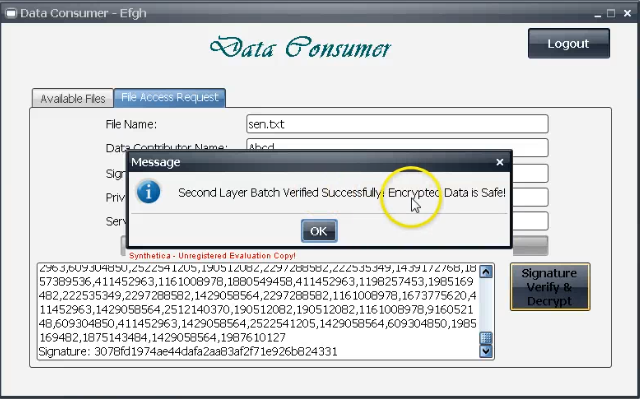




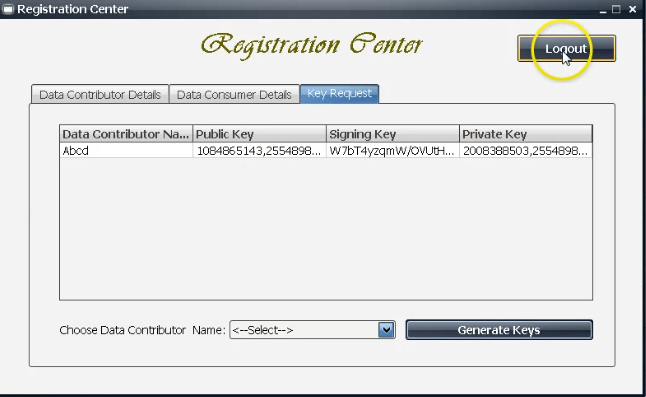










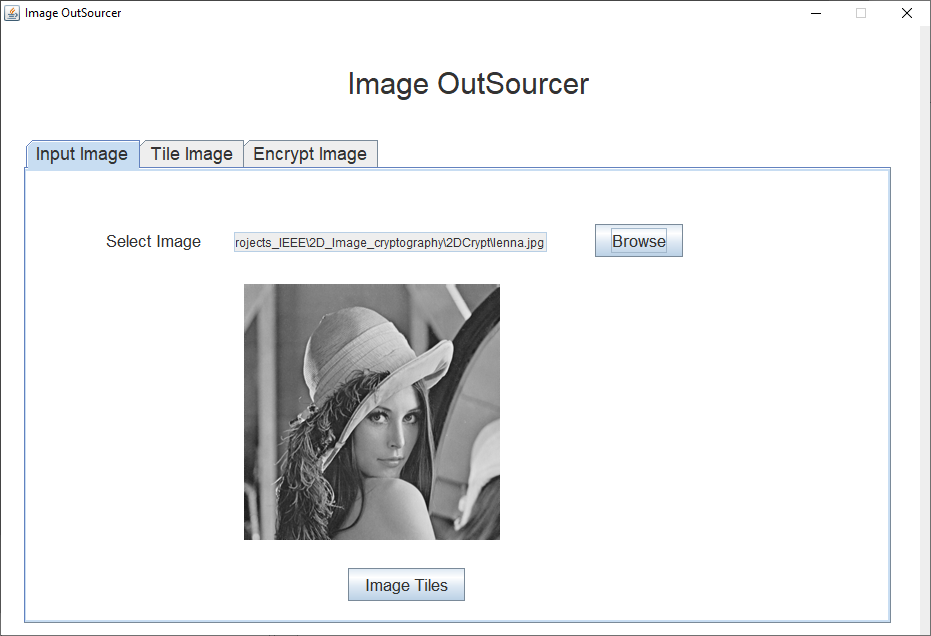

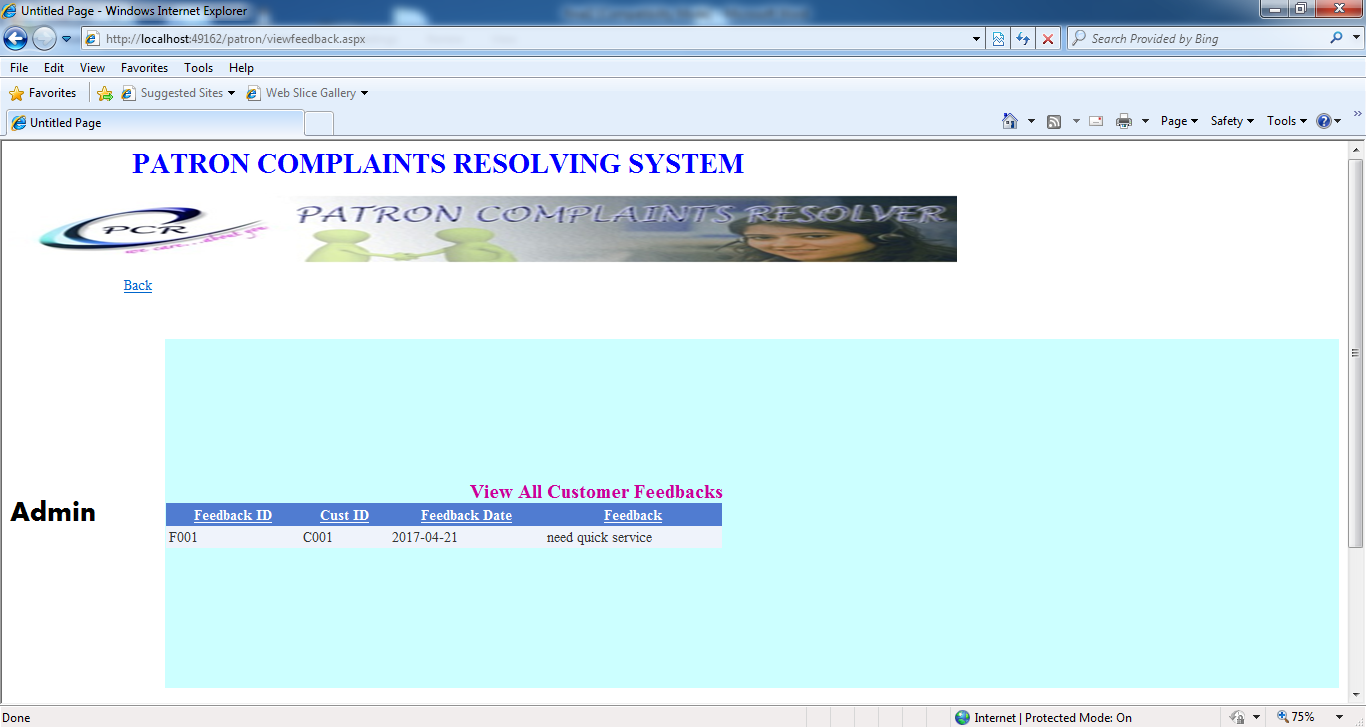

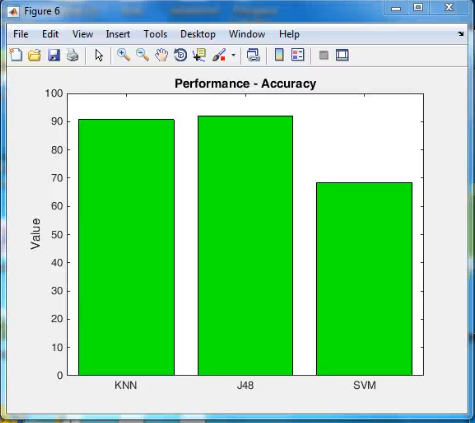

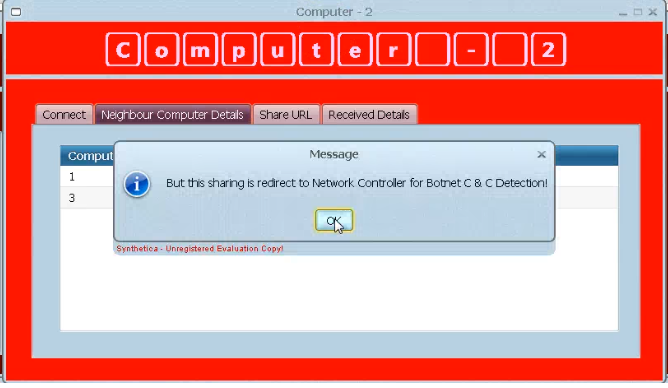




Reviews
There are no reviews yet.