It propose a Trustworthy Service Evaluation (TSE) system to enable users to share service reviews in service-oriented mobile social networks (S-MSNs). Each service provider independently maintains a TSE for itself, which collects and stores users’ reviews about its services without requiring any third trusted authority. The service reviews can then be made available to interested users in making wise service selection decisions. It identify three unique service review attacks, i.e., linkability, rejection, and modification attacks, and develop sophisticated security mechanisms for the TSE to deal with these attacks. Specifically, the basic TSE (bTSE) enables user
s to distributedly and cooperatively submit their reviews in an integrated chain form by using hierarchical and aggregate signature techniques. It restricts the service providers to reject, modify, or delete the reviews. Thus, the integrity and authenticity of reviews are improved. Further, It extend the bTSE to a Sybil-resisted TSE (SrTSE) to enable the detection of two typical sybil attacks. In the SrTSE, if a user generates multiple reviews toward a vendor in a predefined time slot with different pseudonyms, the real identity of that user will be revealed. Through security analysis and numerical results, It show that the bTSE and the SrTSE effectively resist the service review attacks and the SrTSE additionally detects the Sybil attacks in an efficient manner. Through performance evaluation, It show that the bTSE achieves better performance in terms of submission rate and delay than a service review system that does not adopt user cooperation.
- In this paper extend the bTSE to a Sybil-resisted TSE (SrTSE) to enable the detection of two typical Sybil attacks.
- In the SrTSE, if a user generates multiple reviews toward a vendor in a predefined time slot with different pseudonyms, the real identity of that user will be revealed.
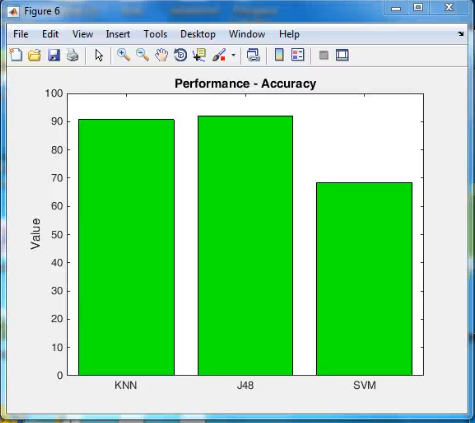
- Through security analysis and numerical results, it show that the bTSE and the SrTSE effectively resist the service review attacks and the SrTSE additionally detects the sybil attacks in an efficient manner.
- The system engages hierarchical signature and aggregate signature techniques to transform independent reviews into structured review chains . This transformation involves distributed user cooperation , which improves review integrity and significantly reduces vendors’ modification capability.
- It presented three review attacks and shown that the bTSE can effectively resist the review attacks without relying on a third trusted authority. We have also considered the notorious sybil attacks and demonstrated that such attacks cause huge damage to the bTSE. We have subsequently modified the construction of pseudonyms and the corresponding secret keys in the bTSE, and obtained a SrTSE system.
- Advantages:
- If multiple reviews with different pseudonyms from one user are generated, the real identity will be disclosed to the public. Security analysis and numerical results show the effectiveness of the SrTSE to resist the Sybil attacks.



























Reviews
There are no reviews yet.