The delay-tolerant-network (DTN) model is becoming a viable communication alternative to the traditional infrastructural model for modern mobile consumer electronics equipped with short-range communication technologies such as Bluetooth, NFC, and Wi-Fi Direct. Proximity malware is a class of malware that exploits the opportunistic contacts and distributed nature of DTNs for propagation. Behavioral characterization of malware is an effective alternative to pattern matching in detecting malware, especially when dealing with polymorphic or obfuscated malware.
In this project, we first propose a general behavioral characterization of proximity malware which based on naive Bayesian model, which has been successfully applied in non-DTN settings such as filtering email spams and detecting botnets. We identify two unique challenges for extending Bayesian malware detection to DTNs (“insufficient evidence versus evidence collection risk” and “filtering false evidence sequentially and distributedly”), and propose a simple yet effective method, look ahead, to address the challenges. Furthermore, we propose two extensions to look ahead, dogmatic filtering, and adaptive look ahead, to address the challenge of “malicious nodes sharing false evidence.” Real mobile network traces are used to verify the effectiveness of the proposed methods.
- Behavioral characterization, in terms of system call and program flow, has been previously proposed as an effective alternative to pattern matching for malware detection.
- In our model, malware-infected nodes’ behaviors are observed by others during their multiple opportunistic encounters: Individual observations may be imperfect, but abnormal behaviors of infected nodes are identifiable in the long-run.
- I identify the challenges for extending Bayesian malware detection to DTNs, and propose a simple yet effective method, look-ahead, to address the challenges.
- Furthermore, I propose two extensions to look-ahead, dogmatic filtering and adaptive look-ahead, to address the challenge of “malicious nodes sharing false evidence”.
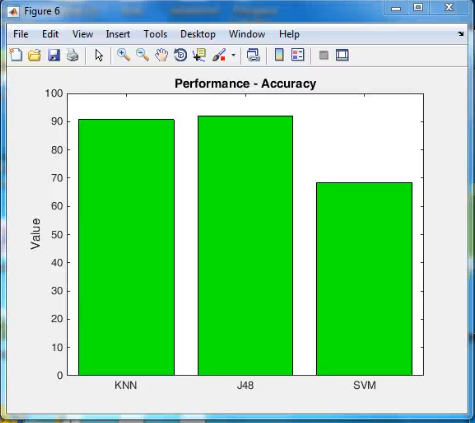
- Assessments come from two models. 1. Household watch 2. Neighborhood watch. The Household watch source node’s own assessments only. The Neighborhood watch source node own assessments with its neighbors’.



































Reviews
There are no reviews yet.