The Internet is vulnerable to bandwidth distributed denial-of-service (BW-DDoS) attacks, wherein many hosts send a huge number of packets to cause congestion and disrupt legitimate traffic. So far, BW-DDoS attacks have employed relatively crude, inefficient, brute-force mechanisms; future attacks might be significantly more effective and harmful. To meet the increasing threats, more advanced defenses are necessary.
- BWDDOS attacks, where the attacker sends as many packets as possible directly to the victim, or from an attacker controlled machines called ‘zombies’ or ‘bots’.
- The simplest scenario is one in which the attacker is sending multiple packets using a connection less protocol such as UDP.
- In UDP flood attacks, the attacker commonly has a user mode executable on the zombie machine which opens a standard UDP sockets and sends many UDP packets towards the victim.
- For UDP floods, and many other BWDDOS attacks, the attacking agents must have zombies, i.e., hosts running adversary controlled malware, allowing the malware to use the standard TCP/IP sockets.
- The first attempts to avoid detection, and the second tries to exploit legitimate protocol behavior and cause legitimate clients/server to excessively misuse their bandwidth against the attacked victim.
- Most BW-DDoS attacks use a few simple ideas, mainly flooding (many agents sending packets at the maximal rate) and reflection (sending requests to an uncompromised server with a spoofed sender IP address, causing the server to send longer response packets to the victim).
- This BW-DDos attack defenses consider four types of defense mechanisms: filtering, rate limiting, detouring and absorbing, and breakthrough.
- Advantages:
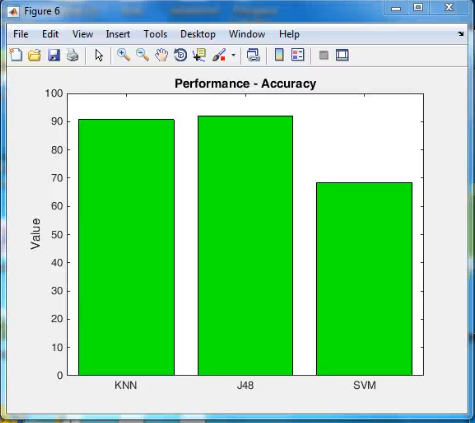
- Bandwidth based Identification
- Easily Identifies attacker
- High attack detection


























Reviews
There are no reviews yet.